newline
Table of Contents
Solving MASTER BOOT RECORD's newest challenge: Personal Computer
GuideMay 14, 2022
The musician MASTER BOOT RECORD, which I’d describe as ‘chiptune synth metal’, does something unique: with every album release, he crafts a challenge, and when you solve that challenge, you gain access to bonus music. The challenges usually involve analysis, cryptography, and other CTF elements. With his new album, Personal Computer, he also created such a challenge. This post explains the steps I took to solve it; read on for spoilers.
Disclaimer: this post contains complete spoilers for the challenge. Don’t read on unless you’re stuck or you don’t care about spoilers.
Start: getting the poem
The challenge starts on the home page for the album: http://mbrserver.com/pc/. There, we have two pieces of information:
-
some binary code:
01110010011001010110111001100101011101110110000101101100011010010111001101101000011001010111001001100101 -
and what looks like base-64-encoded text:
QuXTAUZByO4q13QU8etfs68qb7CUgKo/mzKQ3Itp+4M/WkOnAdWUmi8OylJRZrZvIC81lHGt5+xpdflh 70qRJsznz+FCZ4054NCy4gQnE9p09VR3WhQ284mdORl6XlrBCpT8Z6RXxDoI8Dq7BuA+Vl6gDg+A0c4c 1IIAlzBtzWtKvlGt0Ch2hOrcPOafPiX3rSZz81oOiznAdUWJrfTZYfVuiPU5uX9Co5S1mC5orWM3MmSq 1KizCd3nPw2o1HUlVOm2X3TTySfZWeYJO1S3reMIGjeVXY9eIbfVUn/9gZVA5hcUH4oQXj9JxCICPzB3 HWIEyHzipRkvHVbLgHrVdwuxMnIldTPzMcRAdU7qVqb6tD/KI58n4KEnHAphdJ7qdDQfn3IFSF4i1Tfd xSmU7tAU3fn2UwSwenTVdwXyHpfksmexaBi7zoXvnVEUTb+VDgFOzO3m4JwSIn7hTdEwsnSKFmKWSzDq n6ySLIVAwZt4DAkXn49cJ+Gmiu7ZScJyDzEaSSnzxKzeSzgtCNwvyGjGlGmxLb/T8wPMrNa5VsJ4SdYd NgDVn+e9bV/jQ3QD+2zt2s4ighVkXjGadtdPsemYejZk4RM1HKMau+0id+f3Jbv0qkJmpY4n9jhiFjkJ JQKOqxkbqbCKznyti+RK/Zz/Ejhz3AiwD89M4HAc1SM=
Running the base-64 text through base64 -d doesn’t yield anything readable, so it’s probably encrypted.
On his help page, MBR suggests AES-256, so seems like this is AES-256.
Alright, let’s convert the binary code to a string with Ruby:
bin = "01110010011001010110111001100101011101110110000101101100011010010111001101101000011001010111001001100101"
puts bin.chars.each_slice(8).map { |s| s.join.to_i(2).chr }.joinResult: renewalishere
What if that’s the key to the AES cipher? We open an AES decryption site, choose 256 bit key, paste in the encrypted text, and we get a result!
In the depths of rodent's lair
an enormous code to swallow
turn the words into jpegs
to reveal the way to follow
When the sky is turning black
and there's no moon there to shine
You will find a wall of words
Where the people leave their signs
There's a rider right behind me
who's the holder of the key
Look around and try to find me
In the networks open sea
Once the key is in your hands
Come back home to get your file
One in twenty one you'll find
there still waiting for your trialThe Rodent’s Lair
Hmm, “in the depths of rodent’s lair”…does he mean a gopher hole? That is, the Gopher protocol.
Well, let’s give it a try.
Open up a Gopher client (I use elpher in Emacs), and load gopher://mbrserver.com.
There, we see a pc/ directory, and inside, followme.txt!
Follower
We found the “enormous code to swallow” (the file followme.txt), and the next line of the poem says to “turn the words into jpegs”.
So, we paste the contents of followme.txt into a base-64 to image converter, and we’ve got an image:

This also explains the “wall of words where the people leave their signs”: the graffiti wall in the image.
“Reveal the way to follow”…maybe the image contains GPS data? Yes it does, as exiftool output confirms:
Country Code : ITA
Location : Ostiense
Country : Italy
State : Lazio
GPS Date/Time : 2022:05:12 12:10:04Z
GPS Latitude : 41 deg 52' 10.35" N
GPS Longitude : 12 deg 28' 28.98" E
GPS Latitude Ref : North
GPS Longitude Ref : East
GPS Position : 41 deg 52' 10.35" N, 12 deg 28' 28.98" EPutting the GPS into google maps, we get an approximate location, but not yet what we need.
“When the sky is black and there’s no moon there to shine”: I think we need a different image, in this one the sky is definitely not black. “Look around and try to find me in the networks open sea”…maybe on MBR’s internet profiles somewhere? Going to MBR’s Twitter, we find another picture where the sky is black:

And again, we see the graffiti wall.
“There’s a rider right behind me”…we need to go to the same location as this photo and see what’s on the wall there! After a bit of walking around in google street view, we find where the picture was taken. We also find a rider, who holds the key – his name:

The file found in twenty one
The next part of the poem says, “once the key is in your hands / come back home to get your file / one in twenty one you’ll find”. A file in twenty one…21 is the port for the file transfer protocol!
We use an FTP client to connect to anonymous@mbrserver.com, no need to provide a password.
There, we find pc.rar (as well as a few other files and cool tracks).
Retrieving that file and unarchiving it, we’re asked for a password, which is the key that the rider from the previous section holds.
The final trial
pc.rar contains a readme saying Did you see the code written in the fabric of reality?.
There’s also a WAV file that when played sounds like a regular track, but with some glitches.
Seems like this is a steganography challenge!
We open the WAV file in Audacity, switch from waveform view to spectrogram view, and zoom in to find a code:
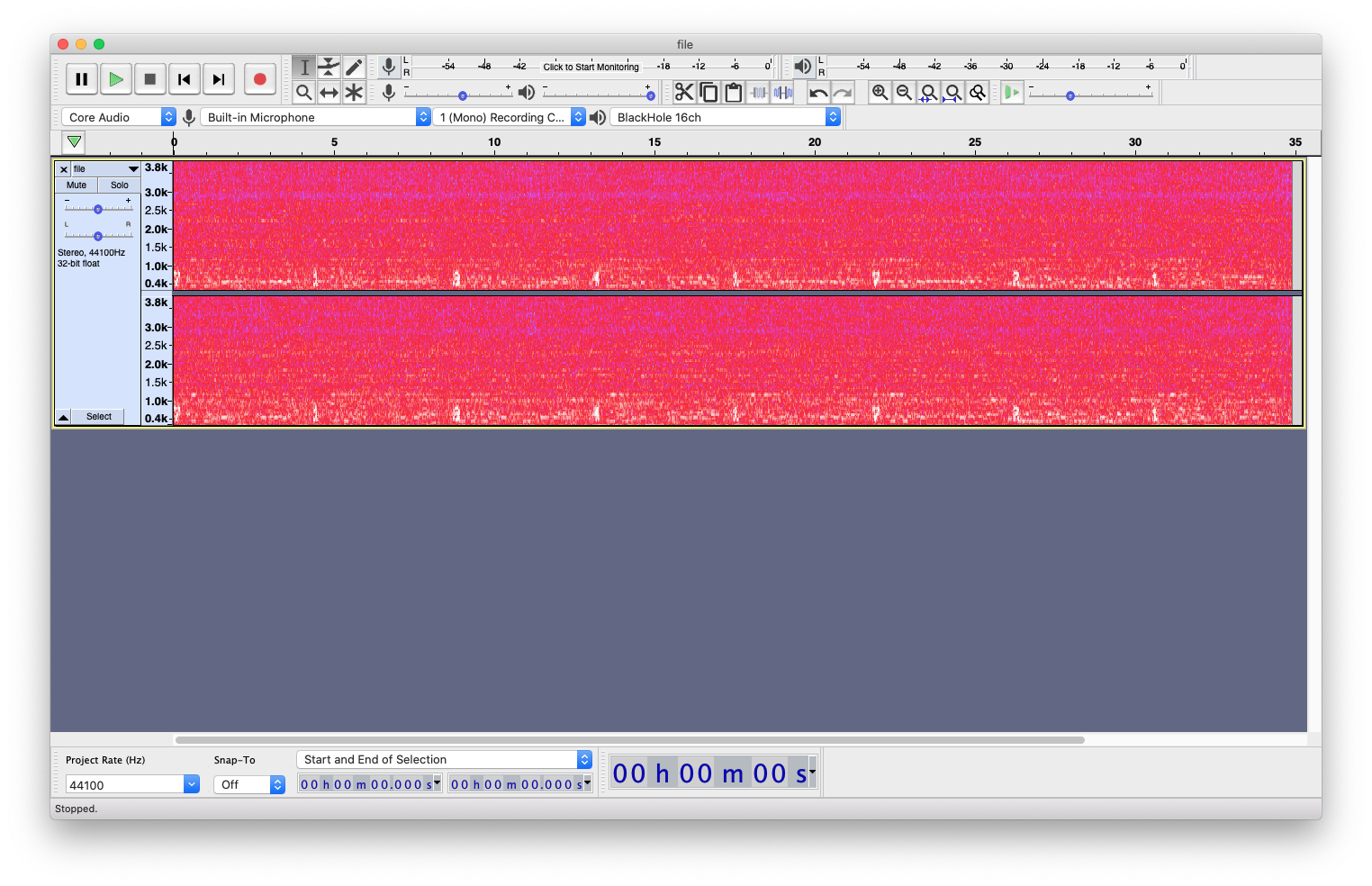
But what do we do with that code?
The readme also says to CALL MY BBS TODAY AND REDEEM YOUR PRIZE NOW!…time to fire up a BBS client!
I use syncterm to connect via telnet to mbrserver.com, and, lo and behold, there’s a message on the BBS from MBR with the subject “PERSONAL COMPUTER”:
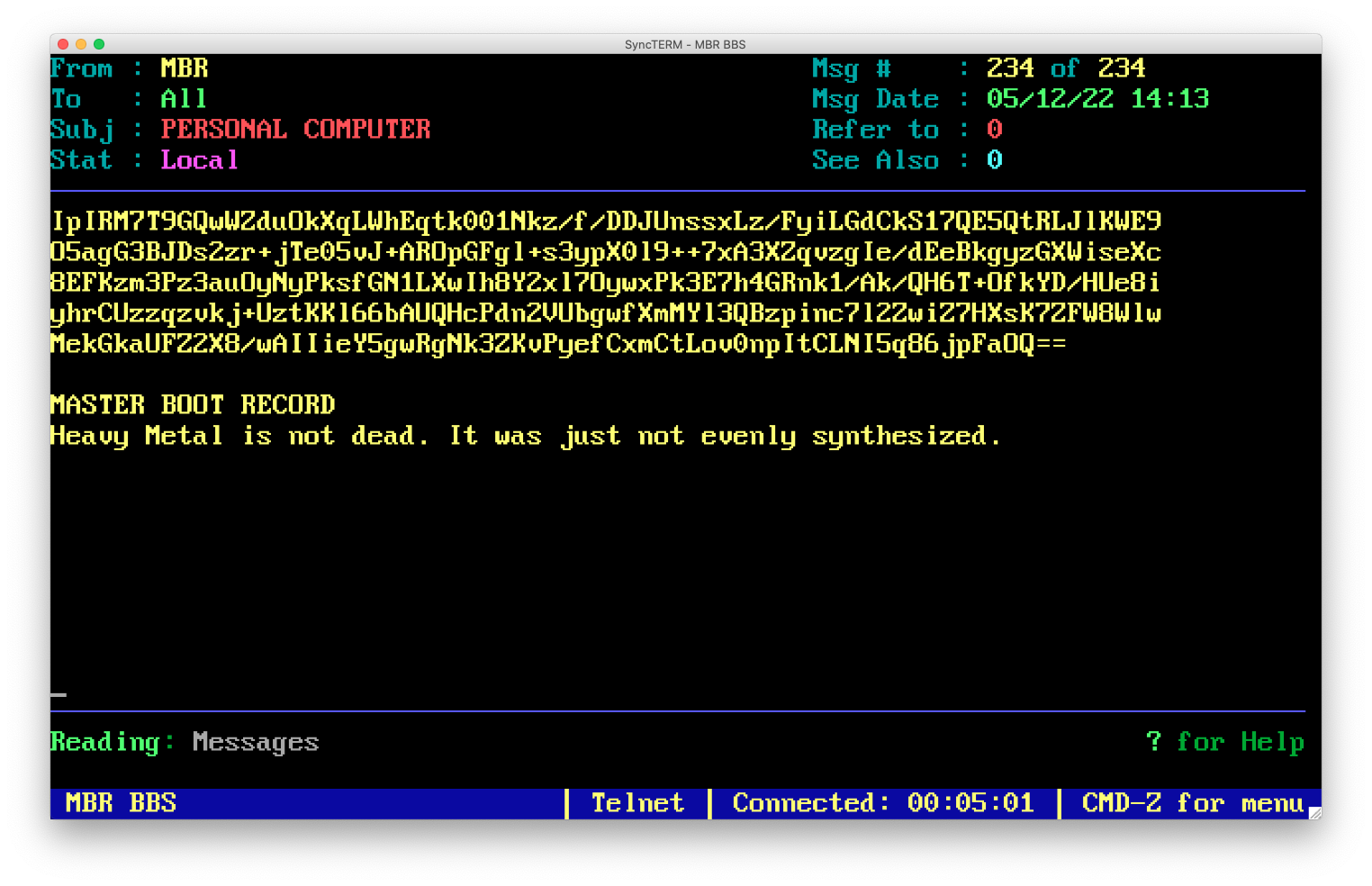
That looks like another encrypted base-64 string:
IpIRM7T9GQwWZduOkXqLWhEqtk001Nkz/f/DDJUnssxLz/FyiLGdCkS17QE5QtRLJlKWE9O5agG3BJDs2zr+jTe05vJ+AROpGFgl+s3ypX0l9++7xA3XZqvzgIe/dEeBkgyzGXWiseXc8EFKzm3Pz3auOyNyPksfGN1LXwIh8Y2xl7OywxPk3E7h4GRnk1/Ak/QH6T+OfkYD/HUe8iyhrCUzzqzvkj+UztKKl66bAUQHcPdn2VUbgwfXmMYl3QBzpinc7l2ZwiZ7HXsK7ZFW8WlwMekGkaUFZ2X8/wAIIieY5gwRgNk3ZKvPyefCxmCtLov0npItCLNI5q86jpFaOQ==Using the same AES decryption website with this string and the numbers obtained from the spectrogram, I get a Google Drive link that points to the bonus track…and it was definitely worth the work. Thanks for the challenge, MBR!